Chief Technology Officer (CTO) of Tether, Paolo Ardoino has recently confirmed that the Tether website faced a DDoS attack. Due to this, the number of requests for the website grew from 2,000 to 8,000,000 on June 18th.
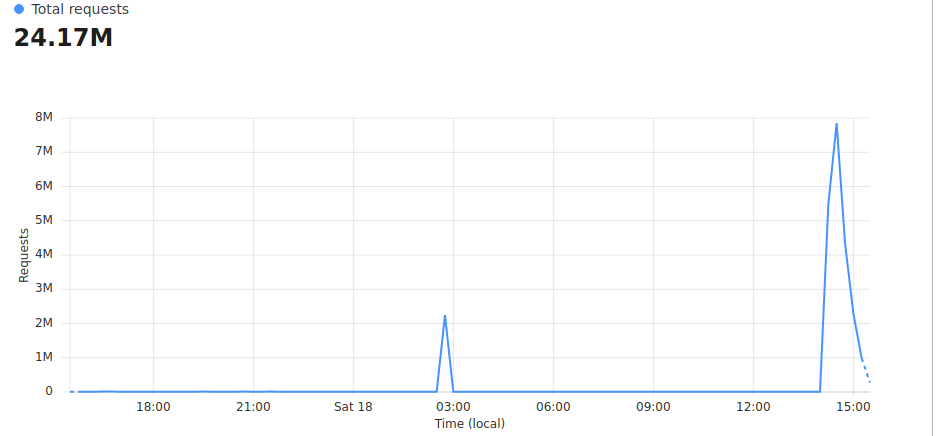
The following image shows the spike of requests that tether.io had recently. Moreover, Ardoino confirmed that they have mitigated the attack. Also, they’ve beefed up the security on the website for the time being.
According to the CTO, the additional security move “won’t affect the ability to redeem”.
Before you ask, DDoS stands for Distributed-denial-of-service. This type of attack disrupts the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
To combat such attacks, Cloudfare DNS management features “I’m under attack mode”. This protects the websites from DDoS attacks by forcing users to complete an additional step to access the website. Basically, the browser completes a javascript challenge that results in a few-second delay.
If the browser is not able to complete the challenge, the user has to complete a captcha on the website.
Usually, DDoS attacks happen via remote servers requesting websites independent of the browser. However, they will fail the challenge request and will not reach the server.
In this case, Cloudflare handles the excess demand leaving the website free to perform tasks as usual.
Coming back to Tether, Ardoino confirmed that the reason for this issue stems from the fact that “it takes a bit of time for the auto-scale to adjust.”
Related Stories:
